By Orlando Trejo (Tech Writer)
It’s 2021 and IT managers and MSP professionals have had to adapt to the new normal. The COVID-19 pandemic has accelerated the inevitable migration of most day-to-day IT processes to the cloud, and working from home is the default.
This shift means embracing new ways of thinking about digital interactions across multiple industries: education, communications, MSPs, etc.
This new digital reality also extends to family meetings and entertainment, changing the nature of tech jobs themselves. We're now seeing a slew of new IT positions emerge such as "Head of Remote Work" emerge. This means that MSPs and IT managers need to make sure their teams are properly trained to face a new generation of cyber threats designed to take advantage of this new normal of remote offices and cloud networks.
The Cyber Attack Pandemic
As soon as most office activities moved online due to lockdowns, we saw the number of cyberattacks surge exponentially. Experts have labeled this as "The Cyber Pandemic." Not only for the sheer number of attacks but also their depth, methods, and the magnitude of complexity involved.
Notable cases of this new wave of pandemic cyber hacks included attacks on COVID-19 vaccine production supply chains, a Bitcoin scam through a breach of high profile Twitter accounts, and a massive US nationwide breach of security infrastructures known as the Solarwind attack.
Millions of automated cyber-attacks take place every minute, targeting companies, individuals, and governments. Even small business owners, bloggers, and freelancers are vulnerable to threats ranging from data theft to impersonation and cyber espionage. Such attacks can originate from anywhere, as shown in the picture below of an example of the geographical locations of attacks to a small personal blog in just 24 hours.
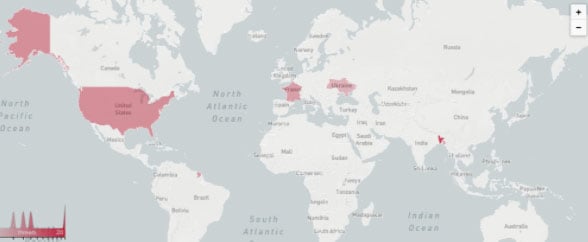
If Fortune 500 companies with humongous IT budgets are still vulnerable to cyberattacks, what strategies can be implemented by medium-sized businesses and startups to enhance their cyber defense? Let's explore five necessary measures IT managers should implement to prevent breaches and attacks to the networks and systems they use every day.
Set Strong Passwords & Two Factor Authentications
Setting strong passwords is an old adage in the IT world. Although experienced IT professionals follow their own set of strategies, there are some basic rules that even non-tech-savvy professionals must follow when it comes to password creation and management:
Avoid Reusing Passwords
There are a ton of online services asking users to create unique login credentials. It may be tempting to create one easily-remembered password for all of them. In terms of network security, this single password for everything is the worst thing you can do since one leaked password could mean a breach on all your accounts. Use a password manager service instead.

Enable 2 Factor Authentication
Passwords are intended to be used to identify users by something only the legitimate user knows.
The downside is that anyone that uncovers someone's password could impersonate the real user. To address this issue, a more robust authentication method needs to be implemented. A second authentication factor: something that only the legitimate users have. This way, it becomes harder to impersonate someone by requiring an additional PIN sent by SMS, or even better: a time-based code sent to the legitimate user's smartphone via apps like Google Authenticator. Make sure that you set up two-factor authentication on all your network access points and email servers.
Customize and Protect Your Passwords
Experienced IT managers have their own personal set of rules for customizing and protecting their passwords. Among the most effective, many IT Managers find that one of the safest methods is writing their master password on paper. Others deliberately set expiration dates and obsessively use password entropy as a strong defense against brute force attacks. Whatever process you use, it makes sense to change it often to decrease the risk of hackers figuring out your password management system, or better still, use a password management service.
Security by Obscurity
We live in an age of information. What’s your favorite ice cream flavor? Anyone can make an accurate guess by going through your social media photos and posts. The restaurant where you had your first date? Anyone checking your Yelp profile or Instagram foodie posts can get an accurate list of your favorite restaurants and dishes. The name of your pet? This common banking security questions may be in plain sight all over your social media.
You may wonder, how is all this information useful to anyone? Well, these bits of information can become clues that lead to a high-value data bounty, such as your server's root password or a key for hackers to reset your banking credentials.
Even top tech firms can unknowingly contribute to providing these chunks of information that can ultimately destroy someone's digital life. One of the most infamous cases was the epic hack of Mat Honan, a senior IT staff writer working for Wired, who lost control of all his accounts when hackers gathered information from his Amazon account and then daisy-chained to other services like Gmail, Facebook, and Twitter. In the end, Mat acknowledged it was his fault for not enabling two-factor authentication on his digital services.
Social media users and influencers are particularly vulnerable to these data leaks, especially those who post photos of their plane tickets and car keys. These photos are, in essence, passwords shouted in the open. This leaves users open to identity theft and other attacks just because they posted that airline ticket or a picture of their new car. Boarding passes include the traveler's name and PNR number, which can be used by hackers to excess your airline reservations and then get even more data like your passport number. Pictures of your car keys can be used to clone the keys by using a CAD program.
At the system security level, we must consider that most attacks on servers and infrastructure are automated, but machines can easily take advantage of human-provided information. For example, below, we can see a log of failed login attempts of a bot trying to access a server by generating automated user/password combinations. We see that most attempts for the username are common personal names and default combinations such as "root, "user," and "test."
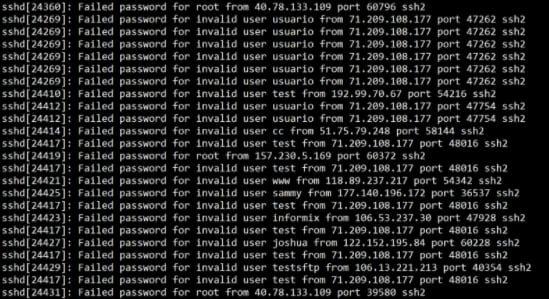
The best strategy to mitigate this risk is to make it more difficult for the machine to guess your passwords by obscuring any information that can lead to your real credentials. Smart IT managers and MSP professionals should change their server's default access settings, such as port 22 for SSH access into another "hidden" port, and also change their default system login credentials. Be especially mindful when posting photos of your car keys or plane boarding passes on Instagram!
Beware of Phishing
According to Cisco, phishing is among the most effective types of cyberattacks and constitutes an increasingly common threat. Any email user has stumbled upon phishing at some point. Phishing emails impersonate a reputable source and can ask for login information, or encourage users to take an action such as to click on a malicious link, or even ask for money. 
Phishing has seen exponential growth in quantity and quality since the Covid pandemic started. A notorious case of this hack in times of COVID-19 occurred when cybercriminals impersonated the World Health Organization (WHO) through Whatsapp messages to get users to click on fraudulent links and inject malware. A phishing research report from Cybersecurity Insiders showed that even the most cautious IT techs could fall prey to phishing attacks when faced with a blast of fraudulent emails.
There are several measures IT managers and MSPs can follow to avoid falling prey to phishing scams, such as:
Be Suspicious And Always On Guard
Doubt the source of any email requesting authentication information or any other suspicious action. Be prepared to pick out phishing scams by reviewing the messages for telltale clues such as low-quality images, misspellings, or the wrong email address.
Check The Message's Original Sender
Fraudulent emails usually come from highly suspicious sender addresses and domains. For example, instead of receiving a message from @apple.com, you might receive one from @7891aplecustomer.xyz, which should trigger your phishing "spidey sense." Take an additional step to block certain kinds of domains that are too long or suspicious from your email server.
A common trend in phishing emails is that they only reference you by your email and never mention your full name or any additional personal information. Also, be suspicious of messages that transmit some urgency, such as "you have only xxx days to verify your account."
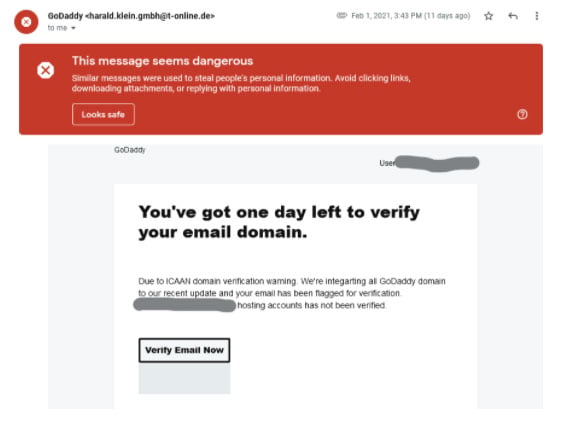
Below is an example of a phishing email trying to obtain credentials to access a GoDaddy account by impersonating an official communication (you can see the sender address has nothing to do with GoDaddy). This is a phishing attempt intended to steal GoDaddy login credentials and then take control of assets such as domains, websites, or entire networks.
Value Hardware & Physical Security
Up to this point, we've only discussed measures to improve your security digitally. It's essential to keep in mind that physical threats can lead to online security breaches and should not be underestimated.
One of the most notorious examples of such attacks was the long-run Supermicro exploit, where small hidden electronic chips were found tampering servers and computers provided by the California-based computer hardware maker Supermicro. This attack affected critical US defense and manufacturing infrastructure, such as the US Department of Defense. Investigations found malicious chips that handled the servers' startup processes while sending confidential data to external locations and downloading malware.
This hardware tampering method has become a pressing issue in Silicon Valley, as the secrets of high tech firms are an attractive target for espionage and sabotage.
IT firms and tech contractors need to be keenly aware that this kind of hardware manipulation is a fundamental threat to their cybersecurity. The most common hardware-based threats include:
A device similar in appearance to a USB stick or a wall charger is attached physically to a computer to record keystrokes. Since this attack lives at the physical user level, keyloggers can bypass encryption and security layers. They can store and remotely send typed input data such as banking or email passwords. The strategy: Be on the alert for suspicious of any devices attached to your workstation.
Hardware-based backdoors undetectable by antivirus software can circumvent disk encryption and other means of digital security. These can be injected during manufacturing in motherboards, disk drives, or memories, such as in the Supermicro case. Thus, companies nowadays are exerting more control over their hardware supply chains and only using equipment from reputable and trusted providers.
Malicious manipulations to the firmware of embedded systems, such as printers, routers, IoT devices, and industrial PLC systems, where attackers install a modded version of the firmware through a simple update process. The strategy for mitigation: keep your firmware updated, and don't use any untrusted USBs.
Be prepared to remotely-wipe your device in case of loss. You can go a step further by encrypting your data in case someone gets unauthorized physical access to your computer or smartphone.
Take Proactive Measures: Firewalls, CDNs, Captchas, and Scheduled Scans
IT managers and online business owners should be aware of the different types of cyber threats and take appropriate action to mitigate risks. We've explored some basic principles to help prevent hackers from breaching your online life: generate strong passwords, embrace secrecy, always being on the alert, and working on physical security.
Nevertheless, any responsible IT manager and MSP should enforce proactive measures that enhance the security of their servers, website, or online business app, by means of expanding their cyber defense arsenal with the following tools:
Firewalls
A security system that monitors incoming and outgoing network traffic. Its primary use is to set up a barrier between your internal network and traffic from the open internet, based on a set of rules. In other words, you get to decide who enters your network (and through which port) and who is blocked.
Content Delivery Networks
A geographically distributed network of data centers can increase the speed of delivery of your internet content, and at the same time, protect your sites from denial of service (DoS) attacks. They are easy to set-up, and popular services include Cloudflare, Fastly, and Stackpath.
Captchas
A set of challenges to protect your blog and sites from spam and fraudulent logins and form submissions by distinguishing human input from bots. The most widely used services are reCaptcha from Google and hCaptcha.
Scheduled Scans
An audit of the network, run automatically and periodically, to look for malicious code. While the server's performance is affected at the moment of the scan, it's generally recommended to run an audit of your servers' status and check for abnormalities at least once a week.
You can use SherpaDesk's integration with NinjaRMM to set up scheduled scans of all your servers to nip in the bud any issues with the servers themselves and detect any external attempts to run malicious code.
What are you doing to keep your network safe today?



%201.png?width=559&height=559&name=close-up-women-working-with-devices%20(1)%201.png)



.png)


